Achieve zero standing privileges without sacrificing productivity
Shrink your attack surface area by reducing standing permissions—without burdening IT or blocking employees from the access they need.
Trusted by IT and Security @







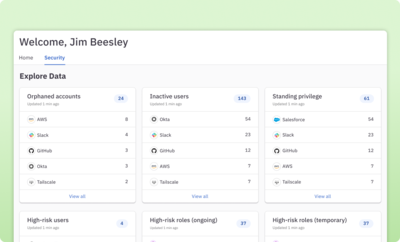
Get a comprehensive view of all access
Create a single pane of glass for understanding identities and permissions in your cloud and on-prem apps, directories, and infrastructure.
Learn more about the identity graph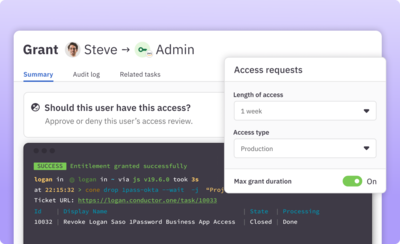
Move privileged access to just-in-time
Move sensitive roles and permissions for infrastructure and cloud apps to just-in-time access that can be requested via Slack, web, or command line. Simple and automated—no help desk tickets required.
Learn more about JIT access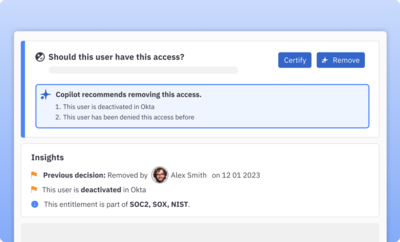
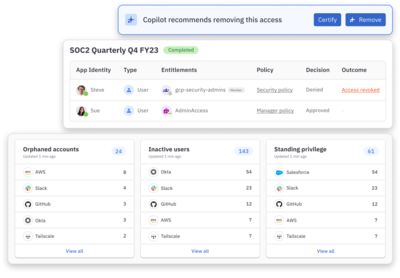
Identify and remediate inappropriate permissions
Leverage fine-grained access queries to discover and remove overprivileged users and use AI-powered access insights to identify and mitigate potential risks.
Learn more about AI copilot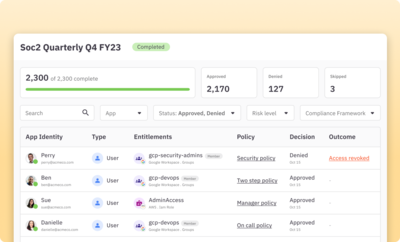
Run fully automated user access reviews
Easily run regular access review campaigns that surface risk-level flags for granular permissions, roles, and groups.
Learn more about access reviews“We are able to significantly reduce our standing AWS permissions by moving to just-in-time access. It's a seamless experience that keeps the team productive and much more secure.”

Julien Colombain
Software Engineer, Ramp

Features
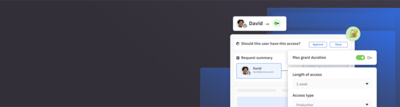
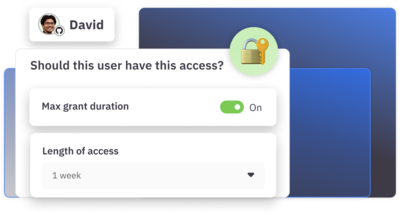
Just-in-time access
Automate JIT provisioning and deprovisioning with flexible policies for temporary, on-call, and break-glass access.
Self-Service access requests
Give users the ability to get the access they need quickly with self-service requests via Slack, web app, or CLI.
Policy-based approvals
Auto-approve low-risk access and build approval workflows that support multi-party and conditional policies for sensitive permissions.
Automated access reviews
Customize and fully automate access reviews that identify problematic access like orphaned or overpermissioned accounts.
Access Copilot
Tap the power of AI to surface access insights based on risk factors like existing privileges, previous decisions, job title, and more.
Out-of-the-box and custom integrations
Integrate your cloud and on-prem apps and infrastructure, including back office and homegrown apps, for complete access visibility.