Secure privileged access to infrastructure
Protect your most sensitive cloud and on-prem infrastructure with just-in-time access, full visibility and monitoring, and account lifecycle management.
Trusted by IT and Security @








Integrate any infrastructure, whether cloud or on-prem
Manage access to cloud-native infrastructure including AWS, GCP, Azure, and Snowflake and self-hosted infrastructure tools like Postgres, MySQL, MongoDb, Active Directory, and LDAP from one control plane.
Learn more about integrations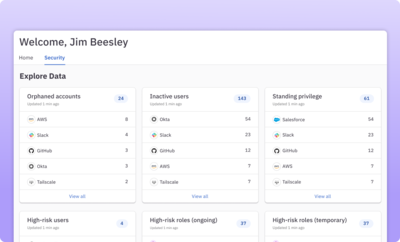
Get full visibility into resources and identities
Get a comprehensive view into access and permissions across your infrastructure and tooling. Quickly identify and remediate high-risk, overprivileged, and standing access.
Learn more about the identity graph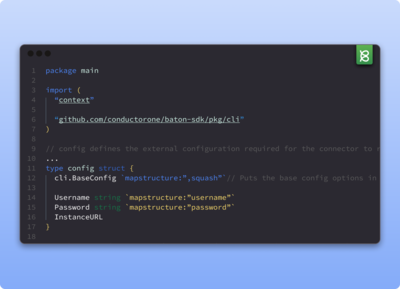
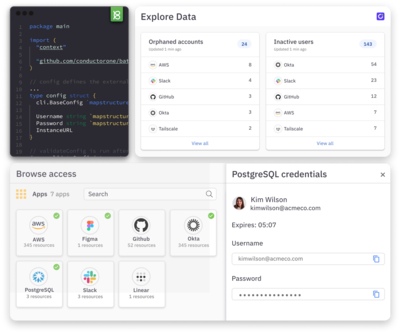
Enforce access controls for your internal apps and infrastructure
Control and monitor access for your business’s most sensitive internal systems. Open source Baton connectors can be quickly deployed or built for your back-office, homegrown, or on-prem apps using our SDK.
Learn more about Baton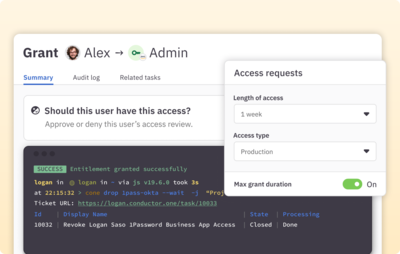
Move to zero standing privileges with just-in-time access
Enforce JIT access to sensitive infrastructure roles and permissions. Provision needed access on demand and automatically remove when no longer needed.
Learn more about JIT access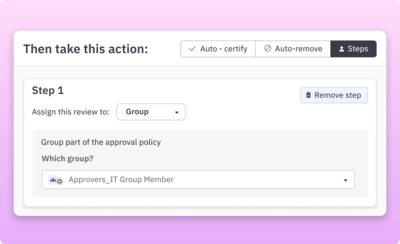
Configure policy-driven access controls
Create zero-touch, conditional, and multistep approval policies. Remove access based on time or changed justification. Force a rerequest for especially risky access.
Learn more about access controls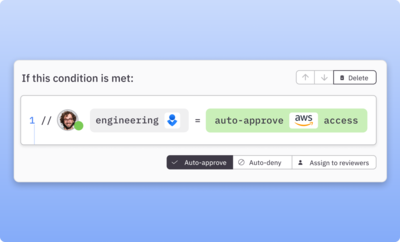
Pre-approve access for on-call users
Use conditional policies to automatically provision JIT access to sensitive infrastructure based on on-call rotations.

Work in a developer-friendly environment
Technical teams love ConductorOne. Configure the platform using Terraform, request access with our command line (Cone), and leverage the ConductorOne API to drive automation.
Learn more about the developer experience“With ConductorOne, we’re able to have a single pane of glass to look at our systems – and manage users, roles, and access to those systems – which is a huge win for us.”

Jack Chen
Director of Information Technology
Features
Out-of-the-box and custom integrations
Integrate your cloud and on-prem apps and infrastructure, including back office and homegrown apps, for complete access visibility.
Policy-based access controls
Auto-approve low-risk access and build approval workflows that support conditional and multi-party policies for sensitive permissions.
Just-in-time access
Automate JIT provisioning and deprovisioning with flexible policies for temporary, on-call, and break-glass access.
Account provisioning
Provision accounts and credentials to sensitive infrastructure automatically.
Unified identity graph
Identify high-risk, orphaned, and overprivileged accounts and visualize access paths for sensitive roles, resources, and permissions.
Developer-friendly tooling
Get a great builder experience with ConductorOne’s open source Baton SDKs, Terraform support, CLI, and API.