Eliminate shadow IT & reduce risk
Talk to our team to learn how we can help you:
- ✅ Control SaaS sprawl with shadow app detection, monitoring, and management
- ✅ Discover OAuth tokens and track all login activity for known shadow apps
- ✅ Lower your overall SaaS costs by bringing shadow apps under management
See how it works
Trusted by IT and Security @







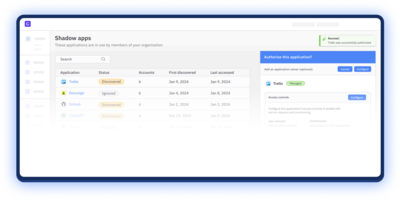
Complete access visibility
Immediately identify and catalog shadow apps for a comprehensive, real-time view into all access
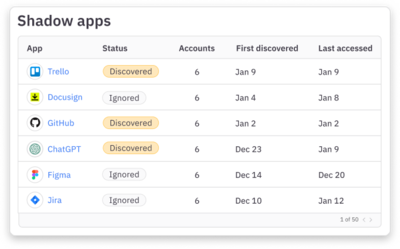
Understand usage
Track all login activity for known shadow apps to determine whether to bring them under management
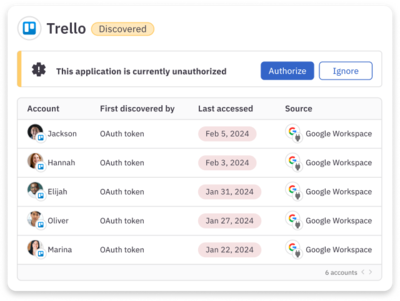
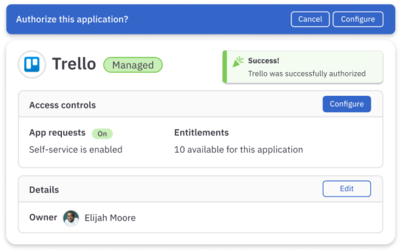
Secure in a few clicks
Authorize shadow apps to bring them under management and enforce fine-grained access controls
Integrations
Cloud
Integrate with your cloud infrastructure, SaaS, directories, data warehouses, and HR systems.

Infrastructure
Connect to your your non-cloud infrastructure, including LDAP, Postgres, Microsoft SQL, and more.

On-prem
Secure your on-premises technology such as Active Directory and homegrown and back-office apps.

Learn how security, IT, and GRC teams use ConductorOne to be more secure and productive
<1month
“Surfacing unauthorized and unmanaged applications was a missing component in our overall visibility. Being able to not only identify these applications but incorporate them into our access controls workflow is solving a big pain point for us.”

Emanuel Francisco
TechOps Team Lead
“It’s set and forget. The time savings from streamlining manual processes related to compliance is huge.”

Jack Chen
Director of Information Technology