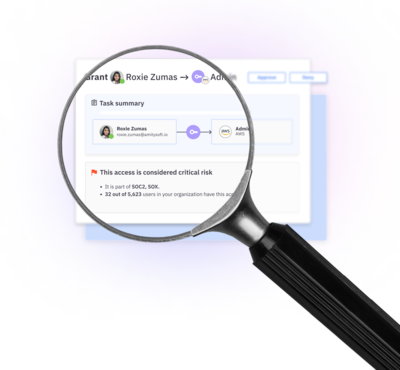
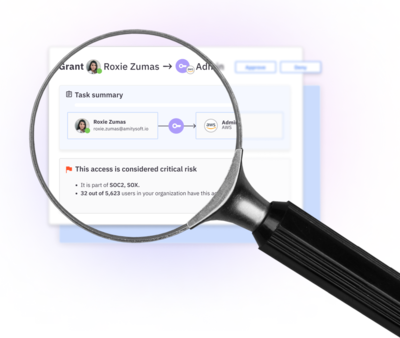
Access has
avisibilitysecuritygovernance
problem
visibility
security
governance
Keep your workforce secure with unified access visibility, just-in-time requests, and automated access reviews.
Trusted by IT and Security @













You can’t protect
what you can’t see

61% of attacks are identity based and 49% of orgs have users with more access privileges than are required for them to do their job
Source

Gain visibility. Govern access.
Improve security.
Automate user access reviews, providing risk assessment and context to make better decisions.
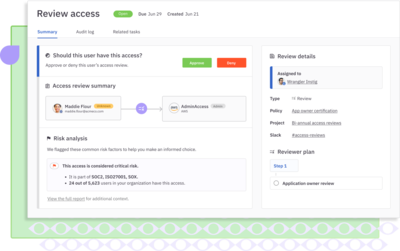
Enforce least privilege with just-in-time access to cloud infrastructure and self-service access to any business app.

Identify and remediate unused, orphaned, and over privileged access.
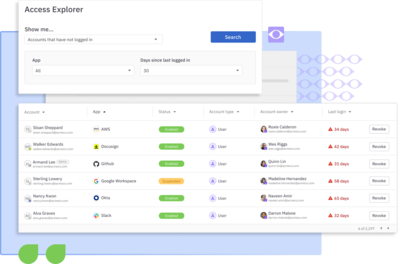


View and manage identity and access from your HR, cloud directory, SaaS, IaaS, on-prem, and homegrown applications.

“We’re able to minimize the number of users with access to critical systems at a given time. That’s a big security win for us across the board.”

Paul Yoo
Head of Security Assurance

“Having a tool that can do this in a timely fashion, iteratively and repeatedly, without manual inputs and outputs enables very real security control. It becomes a really powerful tool–this will improve our security posture at the end of the day”

Tim Lisko
Director of Product and Infrastructure Security