Just-in-time (JIT) access and privileged access management (PAM) are both methods of controlling and monitoring highly privileged access to networks, cloud infrastructure, and critical applications. Both approaches aim to prevent standing privileges and ensure that no user maintains unchecked, ongoing access to sensitive systems.
Each method requires additional criteria before elevated access is granted. This may include stronger authentication, an access request, or an approval workflow tied to a specific task. However, JIT access and PAM are not synonymous.
Important differences between PAM and just-in-time access emerge when you look at how access rights are granted, how long access lasts, and how approvals and audit trails are enforced. If your goal is to reduce standing access, enforce the principle of least privilege, and provide clear evidence of authorization each time sensitive data is accessed, just-in-time access may be the more effective approach.
What is privileged access management (PAM)?
Privileged access management is a security practice focused on controlling, monitoring, and securing access to privileged accounts. These accounts have elevated permissions that allow users to administer systems, manage infrastructure, or access sensitive data.
Traditional PAM solutions typically rely on permanent privileged accounts that are not directly assigned to individual users. Instead, credentials are stored in a secure system. When a privileged user needs access, they authenticate to the PAM solution and check out the credential. This may involve a username and password or an automated connection to the target system.
Once the credential is issued, the password is often rotated so it cannot be reused. To regain access, the user must repeat the checkout process. PAM solutions may also log privileged sessions and record activity for audit purposes.
At its most basic level, PAM acts as a centralized database for managing privileged credentials. However, a PAM implementation only delivers value when paired with best practices like strong access control, multi-factor authentication, granular permissions, and well-defined approval processes. Simply locking away credentials without enforcing least privilege or time limits can add friction without meaningfully reducing security risks.
What is just-in-time (JIT) access?
Just-in-time access is a more advanced form of privileged access management that eliminates standing privileges by granting elevated access only when it is required and only for a limited time.
Unlike traditional PAM, which often provides on-demand access to credentials, just-in-time access provisions temporary access rights dynamically. Access is typically granted in real time based on context such as the specific task, a work ticket, the user’s role, risk level, or the system being accessed.
In a just-in-time privileged access management model, elevated access is time-bound. Once the approved time window expires, access is automatically revoked through de-provisioning. This ensures that even if credentials are compromised, their usefulness is extremely limited.
JIT access systems often integrate with ticketing systems, IAM platforms, and cloud providers like AWS to validate justification and enforce approval workflows. This creates stronger audit trails and clearer evidence of compliance with access policies.
Enforced consistently, JIT access allows companies to get to zero standing privileges (ZSP) and significantly lower their overall vulnerability.
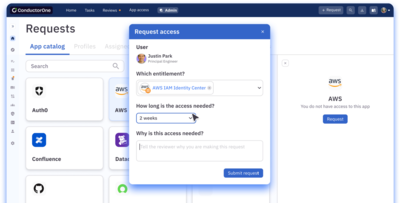
ConductorOne provides seamless JIT access to any app, infrastructure, or resource, with features like self-service requests, smart auto-approval, and no-touch provisioning.
Companies like Instacart have moved 100% of privileged access to automated, policy-based JIT, freeing up valuable security and engineering time. See how they did it:
Why not just use PAM?
Privileged access management can ensure that ongoing access to the protected accounts is unavailable if properly configured. A PAM system typically stores the credentials and provides them on demand. While it may or may not integrate with other monitoring systems, giving access to management systems usually relies on an administrator’s ability to self-determine the requirements for using a privileged account.
This means that anyone who can log in to the PAM system has on-demand access to the credentials used to administer systems and networks. There is no specific time limitation required for any PAM system. If the system allows it, an administrator could log into the system, check out an administrative password, and use that access credential for the entirety of their workday. This practice speeds up their daily activities, but it also greatly increases the risk that they’ll make administrator-level mistakes. To ensure serious mistakes don’t happen needlessly, you should assign the correct permissions and make legitimate privilege elevation frictionless. Otherwise, administrators will look for these solutions to work around the imposition of a PAM system.
Advantages of JIT access vs. traditional PAM
If traditional PAM solutions do not meet the needs of your environment, just-in-time access can bridge the gap. JIT access solutions typically include time-bound access, automated approval workflows, integration with IAM and ticketing systems, and more granular audit trails.
These capabilities reduce the attack surface while streamlining access requests for privileged users.
Static vs. dynamic access
Although JIT access is an incarnation of PAM, it offers advantages over the general static PAM functionality. PAM usually provides constant access rights, regardless of the immediate need. JIT access is dynamic, and it adapts to real-time requirements to minimize unnecessary ongoing access. Unless specifically configured, PAM-owned accounts remain operable and accessible, regardless of whether there is an immediate need for them. The static approach makes for easier management, but it also comes with heightened security risk compared to a JIT access solution. Attackers can exploit the constantly available privileges and concentrate their efforts on evading detection.
Reduced attack surface
JIT access reduces the attack surface by limiting the number of active privileged sessions at any given time. Even if a vulnerability exists, the window of opportunity for lateral movement or misuse is dramatically smaller.
Security and regulatory compliance
Most technology compliance requirements include a section on working with administrative credentials only when necessary. Most daily tasks can be performed with a user’s normal account, not with administrator access. JIT access, often linked to a justification or a work ticket, eliminates the possibility of performing daily tasks (or even casual browsing) with administrative access. When elevated access is not continuous, employees become more aware of the significance and responsibilities of administrative privileges.
While compliance differs from security, compliance with security standards or guidelines can often improve your security posture. JIT access can be a very useful tool for maintaining requirements for security compliance. Many data protection and privacy regulations mandate control over sensitive information access, including elevated access. Organizations must minimize the use of privileged accounts, reserving them only when they are necessary. This may be explicit, as in some versions of the National Institute of Standards and Technology (NIST) requirements, or implied, as with Center for Internet Security (CIS) guidance. In either case, just-in-time access ensures that elevated privileges are not used excessively.
Security awareness
Most employees retain the content of their security awareness training, including the use of minimum necessary privileges. Unfortunately, this does not mean that employees abide by it. There is a significant contrast between the security rules that they accept and their daily behavior.
An organization implementing JIT access reflects a shift from performative training to a deliberate, documented process for granting additional privileges based on clear justification. Employee actions and documentation can be measured against the requirements outlined in the training. This provides concrete data to assess if security awareness is truly embedded in the organization’s culture or if a different approach is needed.
Logging capabilities
Advanced JIT systems incorporate user behavior analytics (UBA) to detect deviations from typical access patterns, an essential part of identifying potential insider threats. This feature is often less developed in PAM solutions. The detailed logging and data richness of JIT systems aid significantly in forensic analysis following security incidents. Investigators can trace actions leading up to an incident more accurately, which is an advantage less pronounced in many PAM systems. JIT systems can automate the generation of compliance reports, a time-saving feature that ensures accuracy and timeliness. This automated reporting capability is often more challenging with PAM systems, where manual compilation might be necessary.
Considerations for using JIT access
Just-in-time access introduces more complexity than basic PAM, particularly during initial setup. Organizations must define access policies, approval workflows, and integration points across their environment.
Setup complexity
Effective JIT access requires automation. Access decisions should consider the user account, device, task justification, risk level, and time window. When implemented correctly, errors related to standing privileges become rare.
Tool integration
JIT access depends heavily on integration across identity systems, cloud providers, endpoints, and applications. Gaps in coverage can introduce operational challenges if not planned carefully.
ConductorOne Integrations
C1 provides pre-built and custom integrations, including support for ephemeral accounts, granular entitlements, and automated de-provisioning across heterogeneous environments.
FAQ
What is the difference between JIT provisioning and SSO?
Single sign-on (SSO) simplifies authentication by allowing users to log in once to access multiple applications. JIT provisioning and just-in-time access control when permissions are granted. JIT provisioning creates or assigns user access dynamically, while JIT access grants temporary elevated privileges for a specific task and time window.
Why choose JIT over the basic PAM approach?
JIT PAM eliminates standing privileges by enforcing time-bound, task-specific access with automated approval workflows. This reduces security risks, limits insider threats, and provides stronger audit trails compared to traditional PAM solutions that rely on static credentials.
What happens when a JIT access mechanism is not available?
When JIT access is unavailable, organizations should rely on tightly controlled break-glass accounts with limited access rights, strong authentication, and enhanced monitoring. These accounts should be audited regularly and used only for high-risk or emergency scenarios.