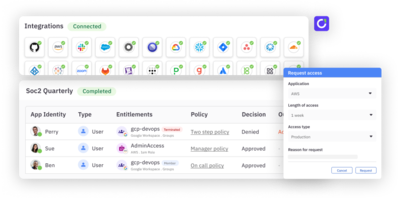
Privileged access management (PAM) is an essential security practice that helps organizations protect their sensitive data and critical infrastructure by controlling access to privileged accounts. These accounts are typically used by system administrators, developers, and other IT professionals to manage and maintain IT systems and applications.
PAM involves a set of processes, policies, and technologies designed to manage, monitor, and audit privileged access to sensitive data and systems. It helps organizations reduce the risk of data breaches, insider threats, and cyberattacks by ensuring that the right individuals have access to the right accounts.
Privileged access management typically involves several key components, including:
- Password management: This involves managing passwords for privileged accounts, including regularly changing passwords, enforcing password complexity requirements, and storing passwords securely.
- Access control: This involves controlling access to privileged accounts based on the principle of least privilege. Access control policies should be based on the specific job functions and responsibilities of individuals.
- Monitoring and auditing: This involves monitoring and auditing privileged access to sensitive data and systems to detect potential threats or breaches. It also involves reviewing access logs and analyzing user behavior to identify anomalies or suspicious activities.
Why is PAM an important security practice?
PAM is a critical security practice that helps organizations protect their sensitive data and systems by controlling and managing access. PAM is a security best practice because it enables organizations to implement the principle of least privilege, reduces the risk of insider threats and cyberattacks, and meets regulatory compliance requirements. By implementing PAM, organizations can improve their overall security posture and minimize the risk of data breaches and cyberattacks.
How is PAM related to IGA?
Privileged Access Management (PAM) and Identity Governance and Administration (IGA) are both important security practices that are designed to help organizations control and manage access to sensitive data and systems.
IGA focuses on managing user identities, roles, and entitlements across an organization’s entire IT infrastructure. IGA solutions typically include tools for managing user identities, defining access policies, and monitoring and auditing user access across the organization.
While PAM and IGA are distinct security practices, they are closely related and often used together to provide comprehensive access control and security management. For example, PAM can be integrated with IGA solutions to provide enhanced control over privileged access, while IGA solutions can be used to manage access to non-privileged accounts and data.
By combining PAM and IGA solutions, organizations can ensure that all user access is managed and audited, from the most privileged accounts to the least privileged. This can help reduce the risk of data breaches, insider threats, and other security incidents, while also improving the efficiency and effectiveness of access management processes.
Summary
Privilege access management is an essential security best practice that helps organizations protect their sensitive data and critical systems by controlling access to privileged accounts. PAM is closely related to IGA and when the two distinct security practices are combined, they work together to create a comprehensive and strong access control and security management system. Implementing PAM allows organizations to improve their overall security posture and minimize the risk of data breaches and cyberattacks.
Get the guide → Best Practices for Privileged Access Management (PAM) for the Cloud