Getting started with JIT access for AWS (using Identity Center)
Before you begin
To complete this guide, you’ll need:
- ConductorOne Super Administrator role
- AWS with Identity Center configured
- Ability to setup an AWS role trust
Estimated time: 30 minutes
Step 1: Integrate your AWS instance
Integrate your AWS instance with ConductorOne. Follow our instructions to set up the AWS v2 connector.
Make sure to select these configuration options on the connector setup screen:
- Enable support for AWS Organizations
- Enable support for AWS IAM Identity Center
Once connected, ConductorOne ingests all of the resources and entitlements for AWS. This includes accounts, roles within accounts, identity center users, identity center groups, and permission sets. You can see all the resources and entitlements by going to Applications > AWS and clicking the Entitlements tab.
Step 2: Configure AWS accounts for JIT access
Now that AWS is hooked up to ConductorOne, set AWS accounts as available for just-in-time access. To do this, we’ll configure access controls for each of the AWS accounts.
Navigate to the Applications page, then select the “AWS” application that was created from Step 1.
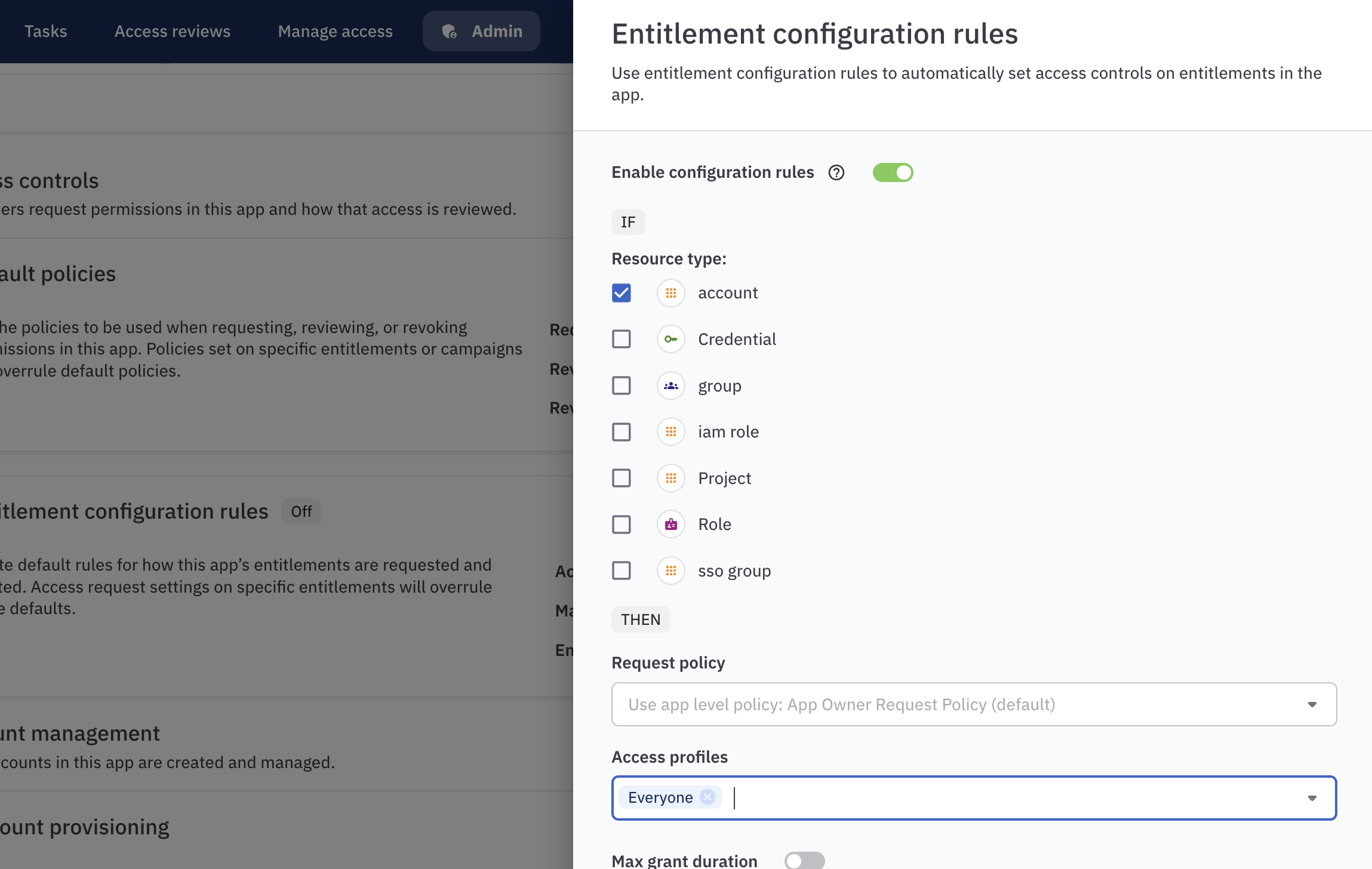
Click Edit in the Entitlement configuration rules in the Access Controls section.
In the configuration rules pane, click the toggle to Enable configuration rules.
Select the account resource type.
Use the Access profiles dropdown to select Everyone.
Finally, check the box at the bottom of the screen and click Apply.
The new settings are applied, and a summary is shown in the Entitlement configuration rules section of the page.
Don’t worry, you can change who can request access, for how long, and the policy for approving access later.
Step 3: Request JIT access
Let’s go request AWS JIT access!
In ConductorOne, click Requests and make sure that App catalog is selected.
Click AWS. A panel opens with the account resources available for you to request.
Click the account you want access to, then click Request on a specific role.
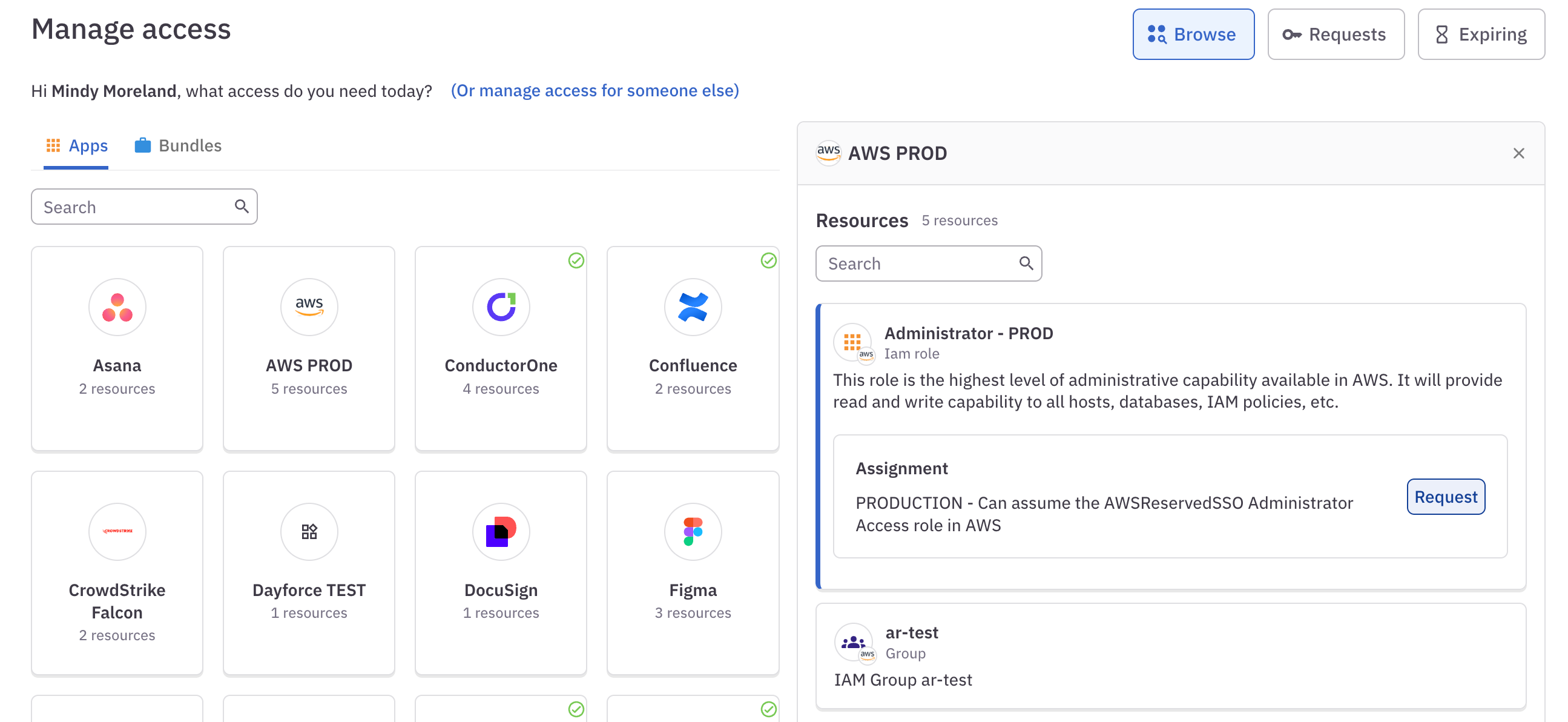
On the Request access form that is shown, select the length of time you want access for.
Click Submit request.
Success!
The request policy routes the request through the approval process. The new access will be automatically provisioned by the AWS connector, and then automatically removed upon expiration.