Administer an active campaign
View campaign progress
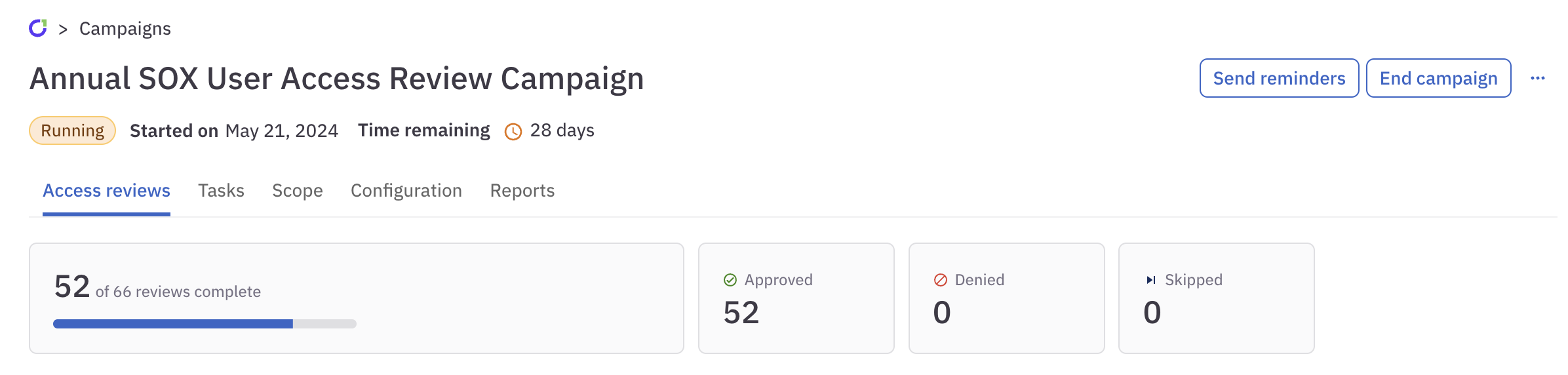
On the Access reviews tab of any campaign, view a dashboard summarizing the campaign’s progress and outstanding tasks.
View and manage individual reviews
On the campaign’s Tasks tab, you can filter the list of campaign tasks, open individual access reviews, view details, and take action:
- See the status of the access review (completed, open)
- See the outcome of the access review (approved, denied)
- Reassign the review, if necessary
- Restart the review, if necessary
- Send the assigned reviewer a reminder notification
- Add comments
- View audit log history
- View related tasks
Send notifications
ConductorOne automates the process of notifying users about their open access reviews, reassignments, and impending deadlines.
Make sure that notification emails reach you: Add no-reply@conductorone.com to your email contacts list.
Automatic notifications
If the Campaign Owner has enabled campaign notifications, these notifications are sent automatically:
| Notification | Time sent | Notes |
|---|---|---|
| Campaign kickoff | When the campaign starts | Sent to all users who have access reviews assigned to them for the campaign. Only sent if the Campaign Owner opts into sending this notification when starting the campaign. |
| Reminder of your open access reviews |
| Sent to all users who have uncompleted access reviews in the campaign. |
| Access review assignment | When a task is reassigned to a new user. | Sent to the user who is now assigned to the access review. |
| Campaign close | When the campaign ends | Sent to all users who were assigned access reviews for the campaign. |
On-demand notifications
To help remind users to complete their campaign access reviews, a Campaign Owner can also send the following notifications on demand at any time during the campaign:
| Notification | Sent to | Notes |
|---|---|---|
| Complete your access reviews reminder | All users currently who have uncompleted access reviews in the campaign. | A campaign-wide reminder. Triggered by clicking Send reminders on the main campaign page. |
| Complete this access review reminder | The user currently assigned to a specific uncompleted access review. | A reminder sent to one individual about one task. Triggered by clicking … > Send reminder in the task details view. |
End the campaign
Campaigns do not end themselves, even if their scheduled end date has passed. A Campaign Owner or someone with the Super Administrator user role must end the campaign.
Click End campaign to finish and close an active campaign. Here’s what happens next:
If any reviews are outstanding, ending the campaign cancels those requests.
When ending the campaign, you’ll be asked if remaining open reviews should be Skipped or Revoked.
The completed campaign is automatically archived on the Completed tab on the Campaigns page.
Depending on the size of the campaign, ending it might take some time. You’ll see a notification popup alerting you when the campaign ending process begins, and another when it’s complete.
Once a campaign is complete, the configuration and access reviews for the campaign cannot be changed. However, you can still view and generate reports for the campaign.
Revoke access that was denied during the campaign
Once the campaign ends, you can manually start the process of revoking access to the entitlements that were denied during the campaign.
Navigate to the campaign’s details page.
On the Access reviews tab, use the Status filter to show only tasks with a Denied status.
If access has already been revoked, an Access revoked message is shown in the task’s Outcome column. If this column is blank for a task, you can revoke the access manually.
Click the … (more actions) menu for the task and select Revoke access. A revocation task is created.
Depending on the revocation policy set on the entitlement, the task might require review and approval before the access is removed by either an automatic or manual process. ConductorOne will create and assign the tasks as appropriate.
Add a revocation step to your campaign’s review policy to automate this process. To automatically kick off a revocation flow for any access denied during the campaign, add a post-execution step to the review policy used on the campaign. See Add followup tasks to learn more.
Generate a campaign report
Access review campaigns have built-in reports that show the progress and prove the outcomes of the campaign. Reports can be generated at any time after a campaign has started. Campaigns and campaign templates can also be configured to auto-generate a campaign report when the campaign ends.
To generate a report:
Navigate to Admin > Campaigns.
On the Running or Completed tab, locate and click the name of the campaign you’re interested in.
Click Reports > Generate report and confirm your action.
The report is compiled for you. Depending on the size of the campaign, this might take several minutes, so please be patient.
When the report is ready, click Download to receive the report in Excel format.
Verify report hashes
If you need to verify the checksum of a downloaded report for auditing purposes, here’s what to do:
Navigate to Admin > Campaigns.
Click the name of the campaign you’re interested in.
Click Reports. You’ll see the file hashes for each report you’ve generated.
If necessary, download the report.
On the command line, navigate to the directory where the downloaded report file is stored. Run the commands appropriate to your operating system, subbing in the name of the downloaded report for <FILENAME>.
Windows
CertUtil -hashfile <FILENAME> MD5 CertUtil -hashfile <FILENAME> SHA256Linux
md5sum <FILENAME> sha256sum <FILENAME>MacOS
md5 <FILENAME> shasum -a 256 <FILENAME>Compare the output of the commands with the file hashes printed on the Reports page. The checksums will match if the downloaded file has not been altered.
Frequently asked questions about campaigns
If an access review campaign due date has passed, can a reviewer still complete their assigned tasks?
Yes, you can complete tasks until the campaign is ended. Only a campaign admin can end a campaign, the campaign does not auto-close on the campaign end date.
For reviewers: If a task is no longer available on the Reviews page, the campaign has ended and no action can be taken. The task can be viewed and comments added under Completed tasks.
For campaign administrators: When it’s time to end a campaign, you will chose what action to take for any uncompleted tasks.
Can a reviewer reopen a task they’ve completed?
Once a review task is completed, a campaign manager or Super Admin can restart the task if needed.
To restart a task:
Navigate to Admin > Campaigns.
Click the name of the campaign, then click Tasks.
Locate the task that should be reopened.
In the more actions (…) menu, select Restart.
Once a task is restarted, the task will be ready for review again on the reviewer’s Reviews page.
Can we delete or remove a task from an in-progress campaign?
Yes, a campaign manager or Super Admin can remove a task from a campaign.
Navigate to Admin > Campaigns.
Click the name of the campaign, then click Tasks.
Locate the task that should be removed.
In the more actions (…) menu, select Delete.
If a task is not automatically assigned to a reviewer and we don’t have a fallback user defined in the policy, what happens to the task?
The task is automatically reassigned to the campaign owners.
If someone leaves the company after the campaign has begun, what happens to review tasks about their access?
If the user who is the subject of an access review task is marked deleted in the system after the campaign has started but before the task has been completed, that task is automatically canceled.