
Crawl, Walk, Run: Solving Your Identity Crisis
·Claire McKennaManaging identity security is increasingly complex, with blind spots, over-permissioned users, and the rise of non-human identities. A crawl, walk, run approach helps organizations gain visibility and automate identity governance for stronger security.
One platform, Every Identity: Announcing Unified Identity Governance for Human and Non-Human Identities
·Brittany SmailAnnouncing Non-Human Identity Governance, a new suite of capabilities that allow ConductorOne customers to inventory, manage, and secure NHIs and AI agents. Govern every identity—human, machine, or AI—from one unified platform.
Some Like It Hot: IGA Hits the Big Time
·Greg HowardThis is an amazing time to be part of the identity landscape. Long ignored, identity is now seen as foundational to security — and companies are catching on, as evidenced by ConductorOne's incredible past year and the success for other identity vendors in the market. Read on to learn why everyone is suddenly embracing identity.
CMMC: What Is It and How to Comply Using Modern Identity Governance
·Brittany SmailAs of December 2024, all contractors and subcontractors working with the US Department of Defense must comply with the Cybersecurity Maturity Model Certification (CMMC) program to protect sensitive government information. Learn more about the CMMC and how to meet its core identity-related requirements.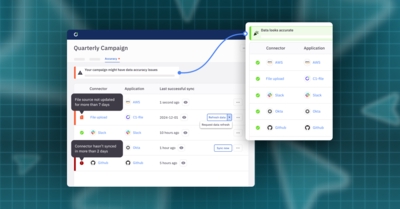

The NIS2 Directive: What to Know and What It Means for Identity Security
·Greg Howard & Brittany SmailAs of October 2024, all EU member states are required to have laws enforcing the NIS2 Directive, a cybersecurity framework aimed at protecting Europe’s critical infrastructure and services from cyberattack. Learn about NIS2, whether your business needs to comply, and best practices for meeting NIS2’s core identity security requirements.
Designing a Great User Experience
·Brittany SmailAs we continue to add new features and deeper capabilities to ConductorOne, our product designers and software engineers have the challenging task of making the platform even simpler and more intuitive to use. Learn all about their approach to UI design and check out our latest UI updates!
Closing the Door on Group Sprawl: Lessons from Spotnana's Security Journey
·Greg HowardGroup sprawl is real—and a major security concern for today's companies. In our latest webinar, Ben Godard, Head of Security at Spotnana, covered the risks created by groups and how to solve them. Here are the takeaways!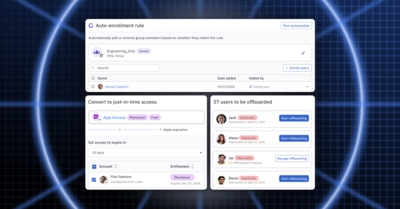
Stay in touch
The best way to keep up with identity security tips, guides, and industry best practices.