

The AI Identity Problem
·Paul QuernaAI agents are changing the identity landscape, but legacy IAM systems weren’t built for them. These fast-moving, ephemeral identities require dynamic access, machine-speed decisions, and a new model of governance. In this post, we break down the AI identity problem—and what it takes to solve it.


The Inevitable AI Wave: Modeling the AI Agent Explosion
·Paul QuernaAI agents are set to outnumber humans 25 to 1—and this blog breaks down what that means for identity and access management. Drawing from the evolution of servers to serverless, learn how companies must rethink their approach now or risk being overwhelmed by an imminent surge of short-lived, high-density AI identities.


Crawl, Walk, Run: Solving Your Identity Crisis
·Claire McKennaManaging identity security is increasingly complex, with blind spots, over-permissioned users, and the rise of non-human identities. A crawl, walk, run approach helps organizations gain visibility and automate identity governance for stronger security.
One platform, Every Identity: Announcing Unified Identity Governance for Human and Non-Human Identities
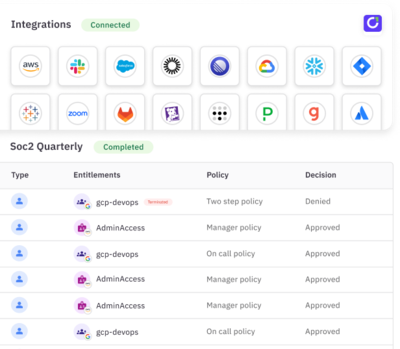
·Brittany SmailAnnouncing Non-Human Identity Governance, a new suite of capabilities that allow ConductorOne customers to inventory, manage, and secure NHIs and AI agents. Govern every identity—human, machine, or AI—from one unified platform.
Stay in touch
The best way to keep up with identity security tips, guides, and industry best practices.