As we kicked off 2026, we focused on continuing to make identity easier for modern organizations.
Identity today is no longer a set of static approvals and quarterly checkpoints. It is continuous, time-bound, and deeply tied to how work gets done across infrastructure, SaaS, and operations. This month’s updates reflect that shift—we focused on making identity governance more dynamic, more self-service, and more observable, while continuing to remove friction from everyday workflows.
A look back at how customers used ConductorOne in 2025
Earlier this month, we shared a personalized 2025 year-in-review with each customer, showing their real usage data across access reviews, provisioning, automation, and policy-driven workflows.
The results reinforced what we consistently hear from teams as they scale their identity programs. On average, C1 customers saved nearly 3,000 hours over the course of the year by using ConductorOne. That’s the equivalent of 25 full work weeks returned to security, IT, and engineering teams. Time that would have otherwise been spent chasing approvals, managing spreadsheets, or manually coordinating access changes was instead absorbed by policy, automation, and continuous governance.
Because we believe in taking our own medicine, we use ConductorOne internally, too. Below is our own 2025 Year in Review, a snapshot of our own product usage.
That reflection helped set the direction for 2026. January’s releases build directly on what customers are already doing successfully, with a focus on making identity governance even more service-oriented, observable, and aligned with how modern teams work day to day.
Turning automation into a governed service
One of our biggest themes in January was rethinking how automation supports end users.
With requestable automations, IT can now expose powerful backend workflows directly to users without resorting to requiring admin access. What used to require custom scripts, tickets, or privileged roles can now be offered as a governed, on-demand service directly from the access catalog.
These automations can collect the right information through structured forms, enforce policy-based approvals, and execute with a full audit trail. Whether it’s onboarding or offboarding, scoped admin tasks, or operational workflows like hardware or environment requests, the goal is the same: allow users to self-service what they need when they need it, without expanding risk.
This is an important step toward treating identity as a service layer that enables safe, self-directed work.
Making reviews faster without sacrificing trust
In January, we introduced batch submission for access reviews to better match how reviewers actually work. Reviewers can now make decisions incrementally, review them holistically, and submit everything at once when ready. This reduces context switching and makes large or complex campaigns feel more manageable.
For admins, new submission tracking makes review activity easier to understand and audit. You can see when reviews were submitted, by whom, and how decisions break down, with exports available for analysis.
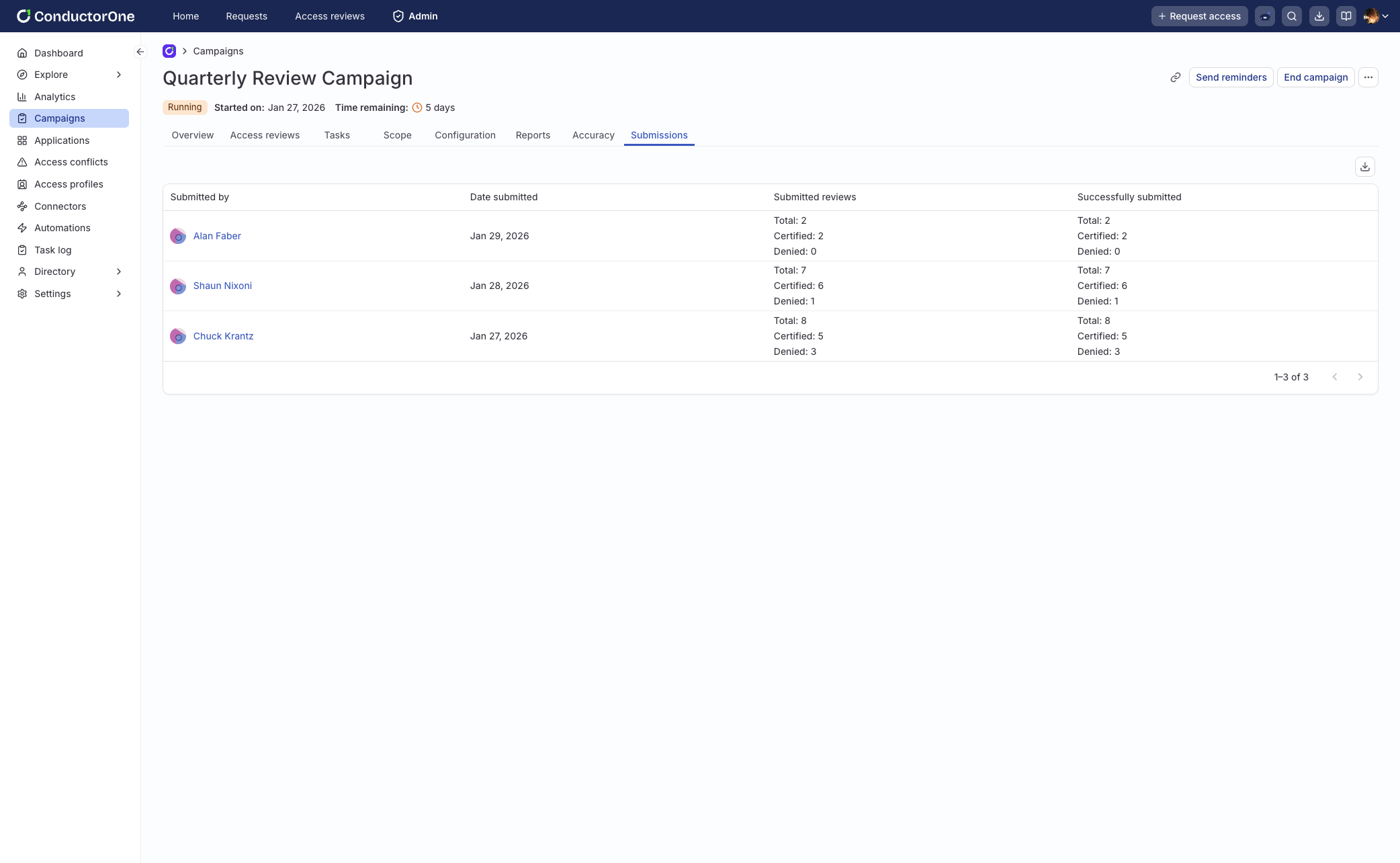
The result is a review experience that is more deliberate, more transparent, and less disruptive, especially at scale.
Visibility into how access really flows
January brought meaningful enhancements to the access operations dashboard. You can now export key metrics, track expiring grants and extension requests, and analyze response times across users and workflows. New percentile-based views make it easier to spot bottlenecks and understand approval behavior beyond simple averages.
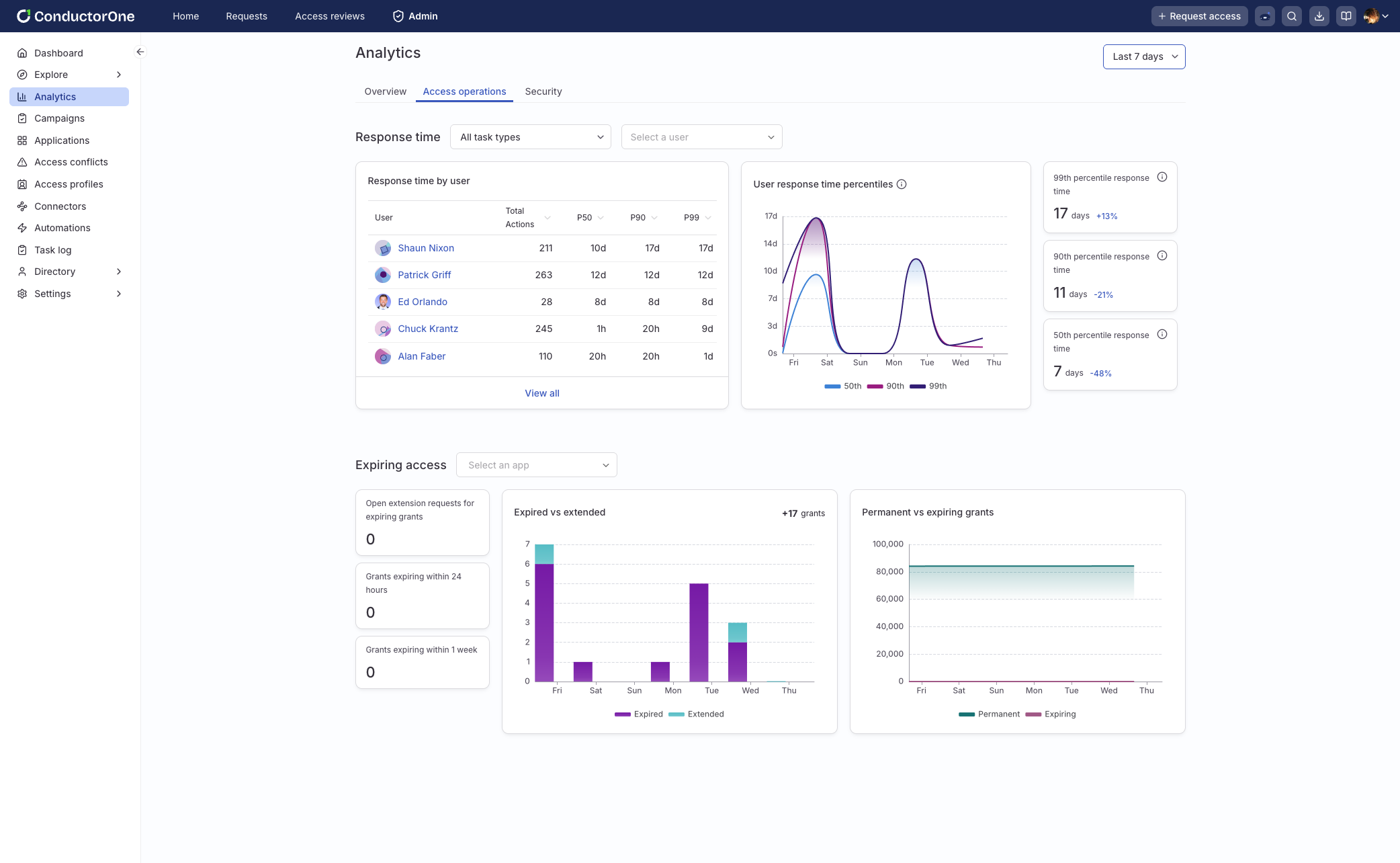
These insights help teams move from reactive cleanup to proactive governance, catching issues before they turn into risk.
Policy and workflow improvements for real-world edge cases
As identity programs mature, edge cases start to matter more than happy paths. Several January updates focused on making policies and workflows more resilient in those moments.
We expanded CEL capabilities to enable more precise, context-aware logic and made it easier to spot and debug mapping errors. We improved how extension tasks behave when accounts are deprovisioned automatically, preserving audit continuity instead of leaving gaps. We added more flexible fallback and SLA handling so workflows do not stall when reviewers are unavailable.
Accessibility, usability, and everyday quality of life
January also included a wide range of usability and accessibility improvements designed to make ConductorOne easier to use for everyone.
End-user pages now meet WCAG 2.0 Level AA standards and we’ve added clearer task icons, better table layouts, alphabetized lists, configurable columns, and more intuitive navigation.
Individually, these updates are subtle. Together, they make identity work feel calmer, clearer, and less error-prone, especially for teams that spend a lot of time on reviews and requests.
January sets the tone for 2026. We focused on making identity governance more service-oriented, more observable, and more aligned with how modern teams operate at speed.
As always, these improvements were shaped by customer feedback and real-world usage. You can find the full details in our weekly release notes, and we’re excited to keep building on this momentum in the months ahead.